Data Execution Prevention (DEP) is a security feature built into the Windows operating system. It is designed to close programs that it detects as viruses or other security threats. Depending upon your CPU, DEP runs in either a hardware-enhanced mode or a software-enhanced mode.
By default, DEP works on certain Windows programs and services. You can, however, customize DEP to have it monitor other programs as well. To do this (if you are using Windows 7), click the Start button, then right-click Computer and select Properties. If you are using Windows 10, navigate to the Control Panel, click System and Security and then click System. This brings up the following screen: (See Figure 1.)

Figure 1. The Computer Properties screen.
Click the Advanced System Settings link at the left of the screen, and Windows displays the Advanced tab of the System Properties dialog box. (See Figure 2.)
Figure 2. The Advanced tab of the System Properties dialog box.
In the Performance group, click Settings. Windows displays the Performance Options dialog box. Make sure the Data Execution Prevention tab is selected. (See Figure 3.)
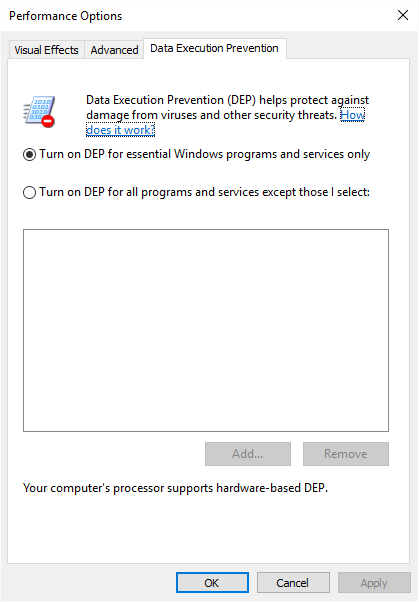
Figure 3. The Data Execution Prevention tab of the Performance Options dialog box.
Note that this is showing the Data Execution Prevention tab, and as you can see, the default action is already selected. If you want to turn on DEP for all programs and services except those you specify, click the second radio button. This enables the Add button. When you click Add, a file browser opens to allow you to select which programs should not be checked by DEP. (You cannot add an essential Windows program or service to be precluded.) When you're satisfied when your selections, OK your way out.
![]()
![]() This tip (12480) applies to Windows 7 and 10.
This tip (12480) applies to Windows 7 and 10.
Part of the security system built into Windows involves notifying you when changes are about to occur to your system. ...
Discover MoreRansomware attacks can cause your system and data to become inaccessible. These dangerous and potentially costly attacks ...
Discover MoreAll objects on your computer (e.g., disk drives) have permissions that allow or deny various types of access. This tip ...
Discover More2019-04-08 21:03:57
Jon Hollmann
The article didn't say which to add, just how to add.
2019-04-08 11:05:09
Malcolm
The original comment was to the effect that an example or two of the sort of program to add to the exceptions list from the "all programs" choice, and the sort of programs one should definitely consider adding.
2019-04-08 10:54:01
Malcolm
One or two examples of the kind of programs one might consider adding would add to one's understanding of this feature - plus a comment on how one make one-off exceptions while leaving the general exception unchanged.
Copyright © 2026 Sharon Parq Associates, Inc.
Comments