There are several types of event logs maintained by the Windows operating system. One of these is the Forwarded Events event log. This log records events written by other computers in the same network ("source computers") that have forwarded their events to the "collector computer." By using the Forwarded Events log, you can keep track of the event logs of several other computers from one central location.
In order to make use of the Forwarded Events log, you have to configure the source computers and the collector computer. From each source computer, run the following command from an elevated-permissions command prompt:
C:\> winrm quickconfig
You must also add the computer account of the collector computer to the local Administrators group on each of the source computers.
Then on the collector computer run the following command from an elevated-permissions command prompt:
C:\> wecutil qc
Finally, you must establish a subscription so that the computers know which events are to be collected on the collector computer. Perform the following steps on the collector computer:
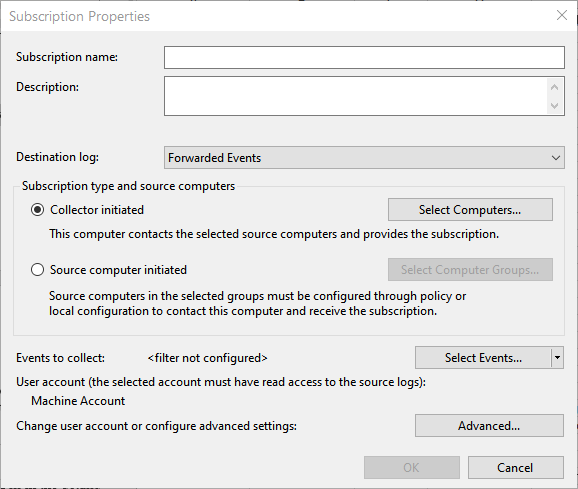
Figure 1. Creating a subscription.
Now the specified events that occur on the source computers will be forwarded to the Forwarded Events log, where you can analyze them all from one machine.
![]()
![]()
![]() This tip (12878) applies to Windows 7, 8, and 10.
This tip (12878) applies to Windows 7, 8, and 10.
Event logs are automatically maintained by the operating system. By periodically viewing them, you'll have a better idea ...
Discover MoreManaging a computer system can often involve a good deal of detective work. This tip looks at how you can use your ...
Discover MoreEvent logs are used to store information about what goes on, behind the scenes, on your system. Whether you want to ...
Discover MoreThere are currently no comments for this tip. (Be the first to leave your comment—just use the simple form above!)
Copyright © 2025 Sharon Parq Associates, Inc.
Comments