There are several types of event logs maintained by the Windows operating system. One of these is the Application event log. This log is used to record events written by applications and services. The applications may be commercial applications, like SQL Server or Exchange, or they may be custom applications that you've developed yourself. The events written to the Application event log can run the gamut from application startup events to shutdown events to "heartbeat" events to run-time error events. The same holds true for events written by Windows services.
Like events written to other event logs, some of the important elements written to the Application log include the date and time when the event occurred, the event ID, and the event source. (See Figure 1.)
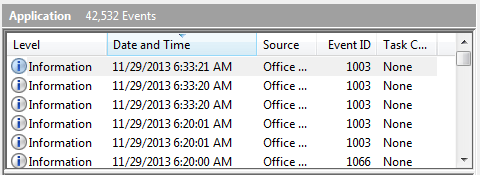
Figure 1. Partial display of the Application event log.
Events can be viewed by using the Event Viewer. By default they are presented in reverse chronological order (i.e., the most recent event is on top). You can, however, sort the events by any of the event columns by clicking the column header.
![]()
![]()
![]() This tip (12886) applies to Windows 7, 8, and 10.
This tip (12886) applies to Windows 7, 8, and 10.
Filtering a log in the Event Viewer allows you quick access to those events you're interested in watching over time. This ...
Discover MoreCreating a custom view in the Event Viewer allows you quick access to those events you're interested in watching over ...
Discover MoreManaging a computer system can often involve a good deal of detective work. This tip looks at how you can use your ...
Discover MoreThere are currently no comments for this tip. (Be the first to leave your comment—just use the simple form above!)
Copyright © 2026 Sharon Parq Associates, Inc.
Comments