There are several types of event logs maintained by the Windows operating system. One of these is the Security event log. Windows writes to this log when auditing is turned on. Writing to the Security log is reserved for Windows only. Other applications cannot write into this particular event log.
Like events written to other event logs, some of the important elements written to the Security log include the date and time when the event occurred, the event ID, and the event source. It's also important to note the Keywords in this log since they indicate what type of audit message the event represents (i.e., "Audit Success" or "Audit Failure"). (See Figure 1.)
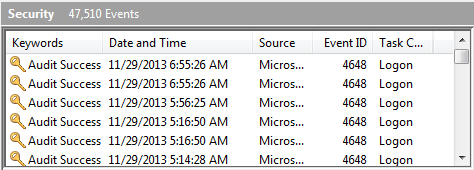
Figure 1. Partial display of the Security event log.
Events can be viewed by using the Event Viewer, and by default they are presented in reverse chronological order (i.e., the most recent event is on top). You can, however, sort the events by any of the event columns by clicking the column header.
![]()
![]()
![]() This tip (12923) applies to Windows 7, 8, and 10.
This tip (12923) applies to Windows 7, 8, and 10.
Event logs are used to store information about what goes on, behind the scenes, on your system. Whether you want to ...
Discover MoreThe System event log holds messages generated by device drivers. This tip explains more about it.
Discover MoreWindows event logs are great resources to see what is "invisibly" going on with your system. By understanding the various ...
Discover MoreThere are currently no comments for this tip. (Be the first to leave your comment—just use the simple form above!)
Copyright © 2025 Sharon Parq Associates, Inc.
Comments